
Bot attack: how Russian mechanism of spreading lies on Internet works
Have you ever received feedback on social media from countless fake profiles that refer to fake accounts of Liberal magazine or Mako portal? Here's how the pro-Russian operators of the new brainwashing campaign work
The Israeli Detaly information and analytical website explained how this works.
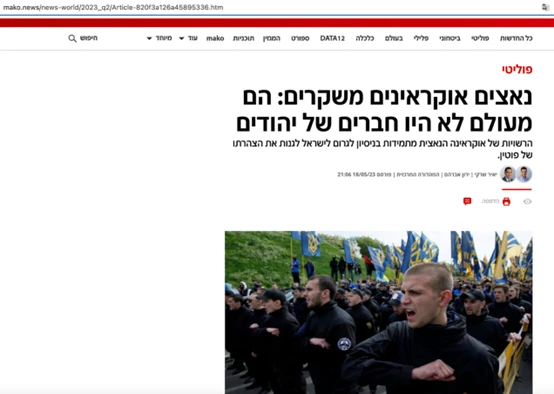
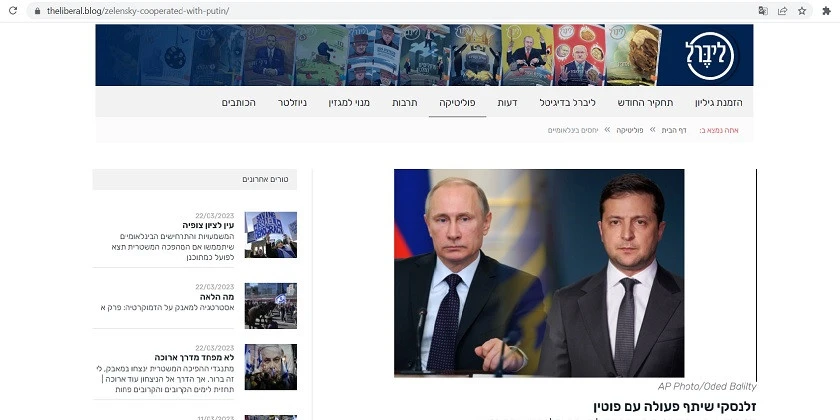
Since June of this year, the Israeli segment of social media has been more active than usual in posting hashtags, statuses, and tweets condemning Israeli solidarity with Ukraine, which has been suffering from Russian aggression. The comments contain links, including to a page imitating the Liberal magazine with the headline "Ukraine is expensive" and an article allegedly written by Joanna Landau, the real author of the magazine, who published a completely different article in it a few weeks ago. Another fake with an article with a similar headline - "Solidarity with Ukraine is very expensive" - imitates the Mako website. The article is signed by a well-known Israeli columnist Amnon Abramovich.
Neither Abramovich nor Landau wrote this material. Neither Liberal nor Mako published them - this is an attempt to influence public opinion in Israel from the outside and move it in favour of Russia and against Ukraine.
Researchers at Liberal magazine tried to find the sources of this disinformation campaign. They note that the deeper you dive into it, the more you see how extensive it is - metastases are found in France, Germany and other European countries. It is obvious that a lot of money has been invested in creating such intricate infrastructure in order to avoid detection mechanisms that could expose both the lie itself and the people behind it. In this article, we will describe where this search has led with a reasonable degree of certainty.
Propaganda and the history of war
Influence operations as part of psychological warfare are not a recent invention. Two and a half thousand years ago, at the Battle of Pelusium, the Persians fighting the Egyptians tied cats to their shields because of an Egyptian belief that prohibited harming these animals. This became one of the factors in the defeat of Egypt and the establishment of Persian rule over it. The Mongols also did not disdain psychological manipulation and sent messengers to the enemy's armies to tell them what horrors awaited them if they did not immediately and unconditionally surrender.
In both world wars of the twentieth century, the enemy dropped leaflets from aircraft onto enemy positions. The Germans on the air of the popular radio station Lord Haw-Haw, which served as a foreign language broadcast in the Third Reich, persuaded American soldiers to desert and return home. During the first war in Iraq, American propaganda persuaded locals to rise up against their corrupt government. And even Israel sent threatening text messages to Palestinians in an attempt to deter them from participating in demonstrations.
A few years ago, the US government reported that in 2016, Russia campaigned during the US presidential election to undermine public confidence in the democratic process in America, to defame Democratic candidate Hillary Clinton and to reduce her chances of winning the presidency. The Americans claim that the Russians are fuelling the fire of public controversy over the BLM movement. China, according to Meta, tried to reduce public support for candidates who were less sympathetic to Beijing during the US midterm elections. Twitter's management has identified similar attempts by Iran. And the list goes on.
The goal of all these "influence operations" is to weaken the other side's cohesion, increase divisions that will draw resources and attention, and sway public opinion in favour of the attackers.
Rough templates
Soon after the Russian invasion of Ukraine turned from a failed blitzkrieg into a war of attrition, an information operation was launched to question the assistance provided to Kyiv by the United States, Germany and even Israel, despite the timidity of its government. The campaign raises the same question: why should taxpayers pay for aid to Ukraine? But it is adapted to different target audiences in different countries. For example, in Germany, the campaign's authors say "America, get out of Europe!", thus interpreting the most famous slogan of the 1960s, "Yankee, go home!". It was used by East German propagandists and is familiar to all Germans. Israelis are frightened that weapons supplied to Ukraine could fall into the hands of Palestinian groups, convinced that the Ukrainian government is linked to pro-Nazi elements, and hinted at the harm that could be done to Russian Jews if Jerusalem takes Kyiv's side in the conflict.
In Germany, the propaganda went beyond the Internet, with graffiti depicting the Statue of Liberty in a sexual position and generously distributed printed flyers that were also circulated online with the slogan "America, get out of Europe!". All these actions together were intended to create the impression that it was a mass movement. However, a closer examination of the photographs showed that graffiti was painted in only one place in East Berlin and printed materials were distributed in another. So it was neither a social movement nor a popular one. But it is certain that someone has invested a lot of money trying to make it look like it is.
To make it harder to identify the source and block their campaigns, the organisers have built a five-layer system of disinformation. Here's what these layers look like.
The first layer
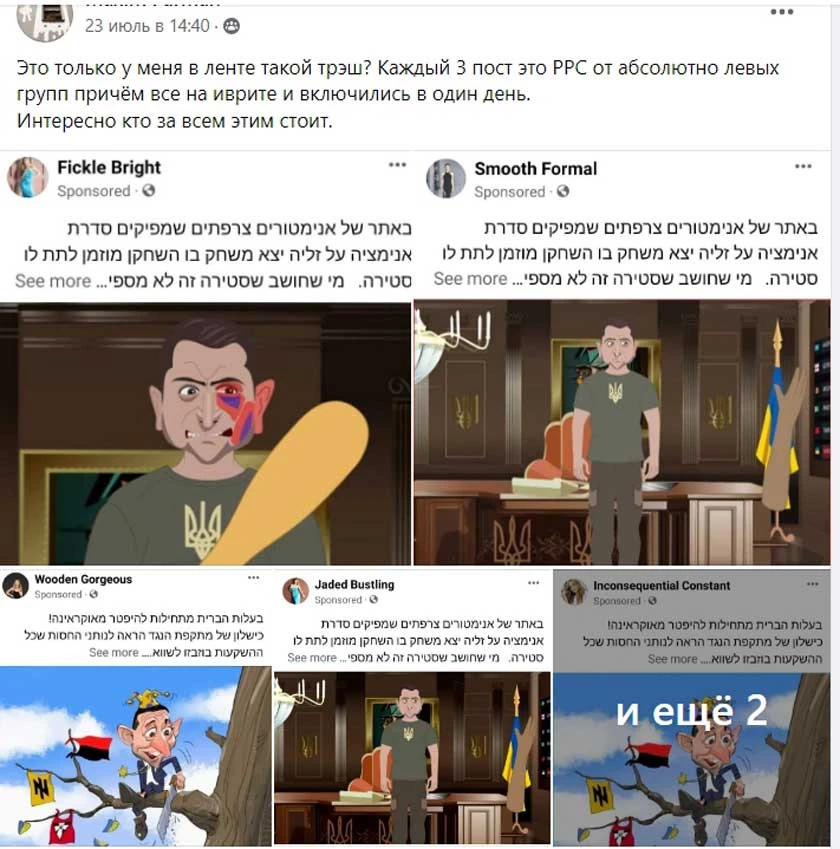
Internet images (accounts with fake profiles) were created in many different channels - Facebook, Twitter and others. Hundreds of such profiles are used to spread links both in their own accounts and in comments to other people's posts. Usually, the link is preceded by a sentence or phrase that matches the spirit of the information campaign.
But this time, unlike other campaigns, its operators acted quickly and bought (or rented) ready-made networks of fake accounts in Turkey, Malaysia, China and some other countries. There are indications that these networks were previously used for cryptocurrency fraud. The content they distributed also looked unnatural: the same profiles distributed messages in English, French, German and Russian, and profiles that had previously "spoken" in Chinese or Russian suddenly switched to Hebrew - despite the lack of any interest in Hebrew materials from their former "followers".
The names of the fakes also seem unnatural, as do the artificially created avatars, often animated, that replace the profile photo.
The second layer
Over the years, social networks have created many algorithms to combat spam and junk content, so a campaign in which someone called Ben Lila sends out the same link to the same article would be quickly detected and blocked. To circumvent this protection, the creators of the propaganda campaign created a second layer: they provided operators with hundreds of unrelated domain names. As a result, instead of a single link to an article, hundreds of links suddenly appear, none of which are similar to each other.
However, they can be identified because the structure of the links leading to the second layer is also patterned: a five-letter subdomain, followed by the domain itself, and then a set of five more characters.
For example, the address leading to the Mako website began with the domain https://jself.nuprotection.co[.]uk/926cf, where jself is the subdomain, nuprotection is the domain (usually a little-known one), and 926cf is the final set of characters. When users clicked on the link published in the first layer (for example, in a social media post or comment), the browser redirected them to a blank page, but contained a social media viewer that displayed the landing page title and photo. The campaign operators achieved this by adding "meta information" in exactly the format that automated social media tools expect. Here's what it looks like in code:
This second-layer preview trick proved to be very effective: the creators didn't have to burn the domains they purchased, and the preview window made the links more attractive. From here, the visitor was transferred instantly (the page refreshed in 0 seconds) to the third layer - the actual page with the propaganda text.
Hosting as a buffer zone
It is important to emphasise that the types of connection between domain name owners and operators of propaganda attacks have not been established: they could have been bought, rented, hacked, stolen, etc. For example, the aforementioned nuprotection domain was purchased in 2016 and is still registered with the former owner, who at least ran an affiliate programme for UK insurance firms until 2018. The other address, ourteam.co.in (discussed below), hosted the website of an Indian internet systems developer until March 2023, and the ownership of the domain was not officially transferred to anyone.
An analysis of IP addresses shows that all these domains access a very small number of servers. And each server has hundreds of such domains. Physically, the servers are located in countries like Finland and Holland, but digging deeper, you can find the addresses to which the reports on the actions are sent, and they belong to Russian companies registered in Moscow and Krasnodar.
The companies hosting these sites provide them with bulletproof hosting. It is supposed to be a barrier between customers and law enforcement agencies. Such hosting companies usually operate in countries whose relations with the West are not warm, or in countries with a weak law enforcement infrastructure. They also generally prefer not to know the identity of their customers at all. To this end, they accept payments only in cryptocurrency, communicate through a bot, and pledge to ignore complaints of abuse as far as possible. The researchers were able to find evidence that at least one of these companies, Zerohost, provided hosting for the Aurora Stealer malware, which was designed to steal information from computers around the world.
The third layer
Unlike the second layer, there are only a few domains here. It serves to make it difficult for those who hunt this network to track down those who operate it. The page that the user will be taken to looks completely innocent at first glance and contains a template text in which nouns alternate with verbs, and the words can change when updated. The phrase may not make sense at all, but this prevents search engines from ignoring it, because in most cases, automatic indexing does not check the consciousness of texts, which means that the page will pass the check.
The base64 JavaScript code at the bottom of the page is another way to avoid detection of counterfeiting by less effective (but, unfortunately, still very common) automated tools. It determines whether the page visitor is a real person. If so, the system will forward it to the fourth, target level.
Recently, the people running the anti-Ukrainian fake news campaign used a website building system from the American company Weblium, even though the company itself clearly declares support for Ukraine on its own website and reports that most of its employees are Ukrainians. After researchers from the Liberal magazine informed the company of this fact, it immediately shut down the sites involved in the pro-Russian information attack.
The fourth layer: management and control
There are several servers here to improve the efficiency of filtering out users from non-target groups and countries - so that they are not redirected to fake pages. For example, users from other countries will not (for the most part) read fake Hebrew pages - they will be redirected either to empty pages or to other sites related to this propaganda attack. The same is true for Germans, French and others. The only country that is present in all of the campaigns, without exception, is Russia, meaning that the Israeli attack is available to users from Israel and Russia, the German attack is available to users from Germany and Russia, and so on. This also clearly proves Moscow's involvement in these actions.
The fourth level is protected by the Cloudflare system of the eponymous American company with headquarters in San Francisco and offices around the world. A website that uses this system routes all its traffic through it and thus "hides in the crowd": data about its location or the identity of its owner can now be requested only from Cloudflare. This company has long been criticised for helping cybercriminals hide. Theoretically, with the push of a button, Cloudflare could have stopped and exposed this entire Russian attack.
The fifth layer
These are the fake websites themselves, with domain names that differ from the real ones. You can see the home pages of TheLiberal, Walla! or Mako, from which real content has been removed and fake content inserted - traces of this remain in the code. But the photos for these fakes were placed by their creators on the servers of the fifth layer, which shows that they are managed from a single centre: the names are consistent, and, for example, the photo "120.jpg" goes to an allegedly "Israeli" Hebrew site, and "119.jpg" goes to one that pretends to be "French". This layer is also protected by Cloudflare, but we were able to narrow down the possible location of the servers hosting the content to the Southeast Asian region with some work.
Lies in Russian
Many factors - similar infrastructures, codes, etc. - indicate that all attacks are being carried out from one centre. In France and Germany, the disseminators of pro-Russian propaganda have made more gross mistakes than in Israel. The campaign being waged these days is wider than the previous ones, with many more servers and domains being used.
The researchers found a placeholder written in Russian on the websites - a helper text inserted into the code. In addition, they found out that the Indian domain ourteam.co.in, which we mentioned above, although it has not officially changed its owner, has been transferred to a server in Moscow and is associated with a person named Zhanna Kambieva. The companies K-POP Partners and First Data are also registered at this address in Moscow (house and apartment).
Many of the domains were registered in Montenegro, but the management has been given to a Russian company since May 2023 - shortly before the first fakes appeared on the web. It may be a coincidence, but the same address in Moscow also turned out to be the domain whistleblowersblog.com, which was once used in a long line of online scams.
Unprofessional work
The concept of the current information attack is similar to the one that the Russians (according to US intelligence) used earlier in the campaign in support of Donald Trump. This was not a hasty action: someone poured a lot of money into buying servers, domains, fake profiles, creating network infrastructure, hiding sources...
Despite this, the implementation of the whole idea is striking in its amateurishness. Language errors and incorrectly constructed sentences reveal that the person writing in Hebrew was not born in Israel and is not a native speaker. With all due respect to Joanna Landau, the Liberal's author, her name is not so high-profile as to draw additional attention to the content published in her name, but the attackers are not familiar enough with the local reality to know this: most likely, when they visited the Liberal's website, they simply took the front page.
The quality of the fake profiles also evokes nostalgia for the old "troll factory". It seems that the leaders of the current campaign bought the cheapest profiles they could find. No attempt was made to give them even minimal credibility. Along with technical errors (for example, the system administrator interface was left open for some reason), the execution is simply disappointing. However, even in 2015-2016, the attack on the US Democratic Party made gross mistakes that allowed the authorities to identify the campaigners and bring charges against them.
The quality of the attacks is more in line with the knowledge of online criminals involved in phishing, credit card and password theft than a serious state system. Obviously, the Russian propaganda apparatus is so worn out that it offers to generate anti-Ukrainian information attacks to extremely incompetent performers.
The article was published with the consent of the editorial board of Detaly.
- News














































